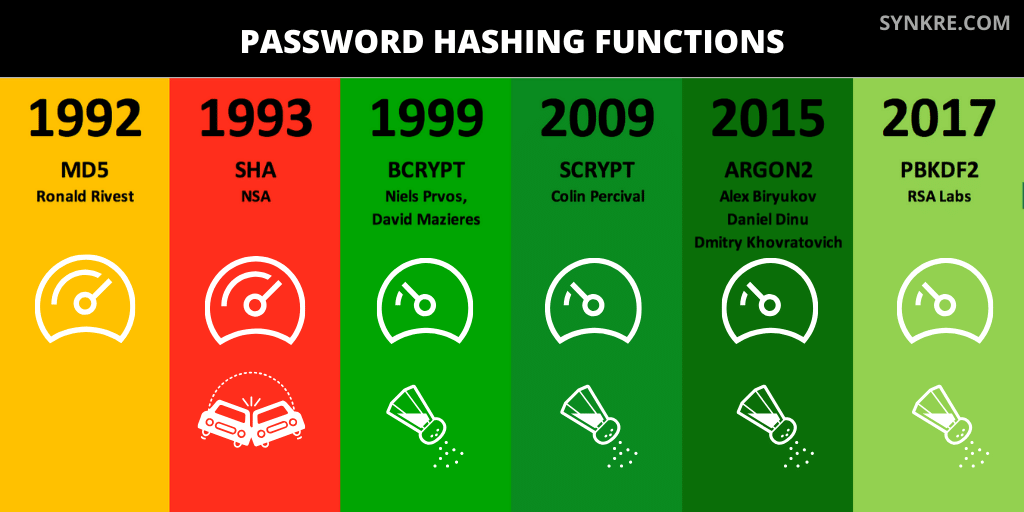
Is bcrypt the best password hashing algorithm?
Bcrypt was designed as an improvement to the Blowfish password hashing algorithm, specifically to reduce the likelihood of 1) brute force attacks and 2) rainbow table attacks becoming successful. It adds an additional cushion of security by modifying the Blowfish key setup in such a way that is more time consuming to produce a key. Bcrypt effectively added more rounds in its hashing function when computing the hash by making the number of rounds configurable and thereby making it a slower hash, and effectively strengthening the key. It reduced the likelyhood of hash dictionary based attacks by simplifying the use of salt, which is known to work against them. With bcrypt a stored password automatically contains random salt, so you have less things to worry about yourself with regards to password storage.
Why does the hashing function matter in brute force attacks?
In brute force attacks, the intruder keeps trying various passwords until one is computed that matches the correct hash. A slower hashing algorithm therefore is more secure because it takes longer to guess the password. In computer security, increasing the required computation time for cracking a key generally results in greater security, because by definition if it takes longer to crack a single password, given a fixed amount of resources, the intruder will be able to break less passwords. Increasing password lengths further increases computation time and therefore password strength.
In addition, increasing the time that it takes to compromise a computer system, makes is more likely that security software or users will detect unusual activity. So by making the number of rounds configurable when computing its hash, bcrypt can be made much harder to break than blowfish.
Limiting the number of login attempts is also useful, In combination with a slow hash this will decrease the likelyhood that that the available time for an attack will be enough to break the hash.
The origins of bcrypt
In 1999, Niels Provos and David Mazières, created bcrypt to increase the security of the Blowfish algorithm. It’s widely used in many Linux distributions and there are implementations of it for all major programming languages. Their paper “A future-adaptable password scheme” was a milestone in the history of cryptographic hashing because with this hashing function the key setup could change over time to account for the advantages intruders gain by utilizing ever increasing computer speeds when cracking passwords.
How many bytes can bcrypt hash?
72 characters is normally the upper limit for passwords using bcrypt, because the algorithm’s mathemetical foundations set this as the upper bound. In reality, 56 characters are usually used in implementations.
Who uses bcrypt and why?
Bcrypt is a password hashing algorithm and it is not the same as just encryption in general. It is used specifically encrypting and securely storing passwords. It is used primarily when a user enters a password and that password needs to be stored in a database in a way that the original password could not be guessed even if the system was attacked and the database got compromised.
Encryption vs Hashing
When hashing passwords there are some special requirements to meet in order to make it harder to crack the password. For example the length of the computed hash, the encrypted stuff that we get once we put our password through the algorithm, cannot be an indication of the password. Password hashing algorithms solve for these problems, specifically addressing attack strategies, that intruders have been using historically.
What is the bcrypt salt?
In order to make it hard to use rainbow table attacks, bcrypt uses a technique in which it not only encrypts your password, but it adds a random string to your password, and it computes the hash for these values together. This hash is then stored in the user database for athentication in the future.
What is a rainbow table attack?
In cryptographic hashing we judge the quality of an algorithm based on how hard or easy it is to guess the original password from the encrypted password. The rainbow table attack technique is based on the idea of building a reverse dictionary for all the possible hashes. It makes use of the fact that multiple passwords can produce the same hash and creates a reverse lookup dictionary without actually finding out what the user’s original password was. It simply creates a reverse look up table so that there would be some entry that produced that hash. Now that entry can be used in place of the user’s actual passwords.
Imagine a scenario, that your user database gets compromised and the attacker now has access to all encrypted passwords. He can now use the above technique to log into any user account
Passwords are more unique with the bcrypt salt
By adding a random string to each password before hashing, we are making them more unpredictable, so that you would be more likely to need a unique key to produce the hash for each user account. This makes it harder to come up with hashes that can break into multiple accounts, especially if those accounts don’t use common passwords.
One way to think of this is how master keys work to open many doors in a building. Adding salt is like modifying all the locks to make them more unique and by that making a master key less likely to work on them.
Where is the bcrypt salt stored?
For example, lets assume that our password is AVeryHard1! In order to store the hash for this password, we would append a cryptographically reliably random string to the password, store the generated hash of this concatenated string, and then next to it we would store the salt in clear unencrypted text, so that at login time, the salt could be added to the user password, the hash could be recomputed, and the result could be compared with what was stored in the database.
The bcrypt password storage is said to have built in salt. What this means is that you don’t have to create a separate column in your database for the salt. The bcrypt hash already has the salt attached to it for simplicity and you can just store it as is.
Can bcrypt be hacked?
When designing a computer system, it is generally safe to assume that no matter what we do, with sufficient time and resources, an intruder would probably be able to hack it. There are no unhackable systems. What we can do though, is to make it very complicated for an attack to succeed and to make it a lengthy process. The longer a successful attack takes, the more time the good guys and security software who are monitoring the system, have to recognize the pattern of activities that are going on and to mount a defense.
Implementations
As stated earlier, one of BCrypt’s “strengths” is that it is readily available, so integrating into your applications is very easy. This reduces the barrier to adding strong crypto to your application.
Java and Scala: JBCrypt
JBCrypt is a very popular Java implementation that I have personally used in projects. It can be downloaded from https://www.mindrot.org/projects/jBCrypt/.
For my own example of how to use JBCrypt from Scala, see https://synkre.com/bcrypt-for-akka-http-password-encryption/
Node: npm bcrypt
To use bcrypt from Node, see https://www.npmjs.com/package/bcrypt.

Comparisons to other hashes
Comparison to md5
Md5 is not suitable to encrypt sensitive information. It can be and has been cracked. It is also a fast hash like the SHA algorithms, but with the additional problem of being directly crackable.
Comparison to sha, sha256, sha512
The sha algorithms are fast hashes and there is no concept of salt. Both of these make them a bad choice for passwords hashing. Password hashing algorithms must be slow and use salt to discourage rainbow table attacks.
Comparison to PBKDF2
This is similar to bcrypt but not quite as secure. PBKDF2 is easier to paralyze and can be made run much faster than bcrypt, which makes it less suitable for password hashing, because password hashing algorthims need to run slow to increase the cost of cracking passwords
Comparison to Scrypt
Increases the memory and parallelism required to cracking passwords, which pushes the bar up by increasing the amount of resources required to crack passwords.
The pros:
Scrypt creates higher resource demand by not simply requiring more memory but by requiring all of it at the same time. Attackers use the latest technology, so GPUs which can access more memory would be an obvious attack vector. Scrypt relies on a data structure it builds to be around and be accessible all at the same time on-going, which GPUs cannot due, and by this it takes away a major tool from intruders. GPUs can access a lot of memory but not simultaneously. It creates a time-memory trade-off, where accessing more memory would be computationally very expensive, and by this it would slow the algorithm significantly, which increases cryptographic strength.
The cons:
In cryptography the age of an algorithm matters. Bcrypt has been attacked for a long time, and we have a good idea about its ability to withtsand attacks. Scrypt is relatively newer.
Bcrypt is available in the forms of many libraries and programming languages, on many operating systems, which means it is very easy to deploy, while Scrypt has less tooling in existence. Since complexity is the enemy of execution, you are more likely to set up strong security if you settle for Bcrypt, simply because it is always right there for you to use.
Comparison to Argon2
Argon2 offers better protection against Time Memory Trade-Off (TMTO) attacks, which became more common with modern GPUs, that can access more memory faster.
Argon2 can be optimized for either time or memory cost, and it has a variant specifically for this type of optimization called Argon2i. Other types of attacks, so called side channel attacks, are also reduced by Agron2’s password independent memory access. It has a variant called Argon2d specifically for this. Side channel attacks rely on weaknesses in the implementation, for example guessing a password from how long a rejection takes when comparing a password, because one can derive what data a loop is processing by the pattern of rejections in a brute force attack, which tries a large number of passwords. By not depending on the user input for memory access, the user loses a way of getting feedback from the algorithm about the data it processes, and so from guessing a password. Yet a third variant, Argon2id is a hybrid of the two, which runs half of the time in Argon2i mode and half of the time in Argon2d mode, providing protection against both styles of attacks.
In addition Argon2 can also be used for Proof Of Work calculations, so it is used in cryptocurrencies.
Is Bcrypt secure in 2020?
Which algorithm is the best for storing passwords depends on a lot of things. As discussed earlier, it is not just the mathematical foundation that matters. While the strength of the hashing function maybe be the dominant factor in brute force attacks, we must also consider how long an algorithm has been withstanding attacks, and how easily available the tools are that allow us to use them, amongst other things,
Bcrypt has provided adequate security for a very long time because it was designed to be adaptable by providing a flexible key setup that could be adjusted to make the algorithm harder to crack (to keep up with hackers) and it has many available libraries which make it easy to set up. In addition, it has been field tested more than the newer algorithms such as Scrypt and Argon2, so we have a lot of data on how it has performed. This still makes it a valid choice in 2020.
Learn more
BCrypt related questions on Stack Exchange/ Stack Overflow: https://stackoverflow.com/questions/tagged/bcrypt